
The main difference between Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) is that TCP is a connection-oriented protocol, and UDP is a connectionless protocol. Both protocols are used to send data over the network, but they do so in different ways. TCP establishes a connection between two nodes before sending the data, while UDP sends the data without establishing a connection first. TCP is more reliable since it ensures the data will reach the destination node, while UDP does not guarantee this. Additionally, TCP provides error correction and flow control features not presented in UDP. Therefore, it is essential to understand these two protocols’ differences to choose the one best suited for a given task.
Communication protocols are essential for the efficient operation of network systems. TCP/IP and UDP are commonly used transport protocols that enable data exchange. This blog post will explore the differences between TCP/IP and UDP by examining their features, functions, uses in real-world applications, and essential factors to consider when choosing between them. Network managers can make the best decisions by understanding these features and differences.
Communication protocols are rules that govern the exchange of information over a network. They enable connected devices to communicate with each other without requiring any detailed knowledge from their user. Protocols provide a common language for digital data transmission, allowing computers and other connected devices to interact with one another efficiently. Without such protocols, it would be virtually impossible for users to access web pages, use email services, or communicate online.
Protocols are responsible for managing data transmission over networks through various techniques. They provide encoding methods, such as compression and error correction, that help ensure accurate delivery of messages. They also define how data is addressed and routed across networks by determining which computers should receive a message and how it should be sent to its destination. Protocols also establish rules for data flow control, which help manage the flow of information efficiently. By carefully managing these factors, communication protocols enable reliable and secure data exchange between connected devices.
TCP/IP, or Transmission Control Protocol/Internet Protocol, is a set of communication protocols that enable data exchange across networks. It is the primary protocol for communication over the Internet and other large computer networks.
At its core, TCP/IP is a connection-oriented protocol that allows for reliable delivery of messages between computers. This means that, for two devices to communicate, they must first establish a connection. Once this connection is established, data can be transmitted to the receiving device with minimal disruption. TCP/IP also includes features that help ensure accurate delivery of messages, such as error checking and correction.
TCP/IP is used in many everyday applications and services requiring reliable network communication. It is used for email and file transfer applications and web browsing. Voice over IP (VoIP) technologies, such as Skype, also rely on TCP/IP to enable voice communication over the internet. Additionally, it is crucial for many networking protocols that allow computers to communicate with each other on a local area network (LAN).
UDP, or User Datagram Protocol, is another commonly used protocol for network communication. UDP is a connectionless protocol, unlike TCP/IP, based on a connection-oriented model. This means devices sending messages do not need to establish a connection before data transmission. UDP can provide faster transmission speeds and lower latency than TCP without creating and maintaining connections between two computers.
However, UDP is an unreliable protocol, meaning that data sent through it may not always reach its destination or arrive in the order it was sent. This can benefit certain applications where accuracy is less important than speed, such as streaming media or online gaming. The lack of reliability also means that UDP requires less overhead since there is no need to ensure accuracy for delivery.
Common applications that rely on UDP include video streaming, gaming, Domain Name Service (DNS) lookups, and Voice over IP (VoIP). These services are particularly well-suited for UDP due to the protocol’s fast transmission and low latency.
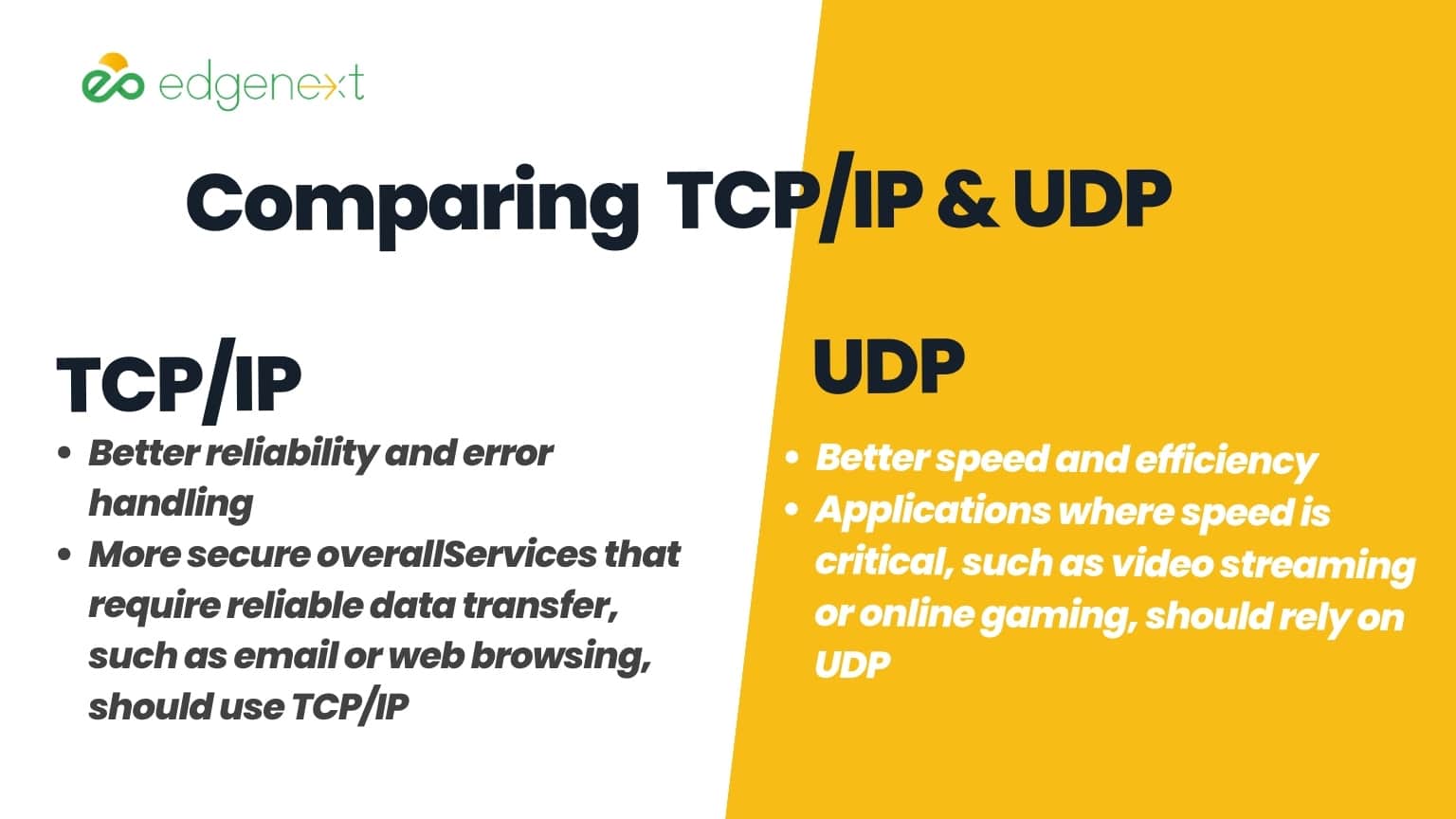
Regarding reliability and error handling, TCP/IP is the clear winner. It includes features such as data compression, error correction, and flow control that help ensure accurate delivery of messages. UDP does not provide these features, so there is no guarantee that data sent over this protocol will reach its intended destination or arrive in the same order it was sent in.
In terms of speed and efficiency, UDP is the superior method. Since it does not require connection establishment before data transmission, messages can be sent faster and with lower latency than TCP/IP. Additionally, its lack of error correction features also means that it requires less overhead for data transmission.
Due to these distinctions, different use cases and applications are better suited for TCP/IP or UDP. Generally, services that require reliable data transfer, such as email or web browsing, should use TCP/IP. On the other hand, applications where speed is critical, such as video streaming or online gaming, should rely on UDP.
Finally, it is crucial to consider security considerations when choosing between TCP/IP and UDP. Both protocols can be secured using encryption, but TCP/IP is more secure overall due to its connection-oriented model. Additionally, some applications may require using one protocol over another for security reasons, such as VPNs, which typically rely on TCP/IP for data transmission.
Several factors must be considered when choosing between TCP/IP and UDP. The application type is one of the crucial factors to consider when selecting a protocol. As mentioned, services requiring reliable communication, such as email or web browsing, should use TCP/IP. At the same time, applications that prioritize speed over accuracy, like video streaming and online gaming, should rely on UDP.
Network conditions are another critical factor to consider when selecting a protocol. For example, suppose a network is experiencing high packet loss. TCP/IP may be the better option since it is designed for reliable communication over networks with varying conditions. On the other hand, if latency is the biggest issue, UDP may be more suitable due to its faster transmission speeds and lower overhead.
Finally, it is crucial to consider any specific requirements of the application or service in question. Some services, such as Virtual Private Networks (VPNs), may require a specific protocol for security reasons, typically TCP/IP. Additionally, some devices may not support one protocol over another, so this should be considered when selecting a protocol.
Real-world applications of TCP/IP and UDP can be seen in various industries, from banking to gaming. For example, secure transmission of financial data over networks is critical in the banking sector. As such, many banks use TCP/IP to ensure reliable communication between systems.
In the world of gaming, meanwhile, speed and low latency are paramount for a positive user experience. Online multiplayer games, such as first-person shooters and racing games, rely heavily on UDP for fast data transmission and minimize lags. These case studies reveal some practical differences between TCP/IP and UDP. The banking example shows that services requiring secure communication should use TCP/IP, while the gaming example highlights how UDP is better suited for applications that prioritize speed over accuracy.
The future of TCP/IP and UDP will likely be shaped by emerging technologies, such as the Internet of Things (IoT). As more devices connect to networks, there is an increased demand for reliable communication and speed. To meet these needs, modifications or additional features may likely be added to both protocols to improve performance and security.
Overall, it is clear that TCP/IP and UDP usage will continue to evolve with emerging technologies. Users can better leverage these protocols by considering potential modifications and applications. This will help ensure network communication is as secure and efficient as possible to get the most out of our connected devices.
In conclusion, it is vital to understand the differences between TCP/IP and UDP when communicating over networks. TCP/IP provides reliable communication with assurance that data is being sent and received as intended, while UDP offers faster transmission speeds with minimal overhead. Understanding these protocols in various technological contexts cannot be overstated. Knowing which protocol to leverage can significantly impact the performance and security of applications and services communicating over networks.
At Edgenext, we understand the importance of leveraging the appropriate protocol for communication over networks. Our range of data security solutions is designed to help protect your business from threats while optimizing performance and efficiency. Contact us today to learn more about how we can help you maximize the benefits of TCP/IP and UDP in a secure and efficient environment.
© 2025 EdgeNext Copyright All Right Reserved