Distributed Denial of Service (DDoS) attacks are cyber-attacks that can disrupt and take down websites and other online services. DDoS attacks involve flooding a system or server with malicious traffic from multiple sources as a means of overwhelming the resources. This prevents legitimate users from accessing the service, resulting in prolonged downtime and potential financial losses for the business. Companies must have strategies to defend against and mitigate these attacks. This blog post will provide an overview of the different types of DDoS attacks and discuss how businesses can protect themselves against them.
A DDoS attack is a type of cyber-attack that targets websites and other online services. The attacker uses multiple sources to send large amounts of malicious traffic to the target. This overwhelms the system and prevents legitimate users from accessing it, resulting in prolonged downtime and financial losses for the business. DDoS attacks can be categorized into volumetric, protocol, and application layer attacks.
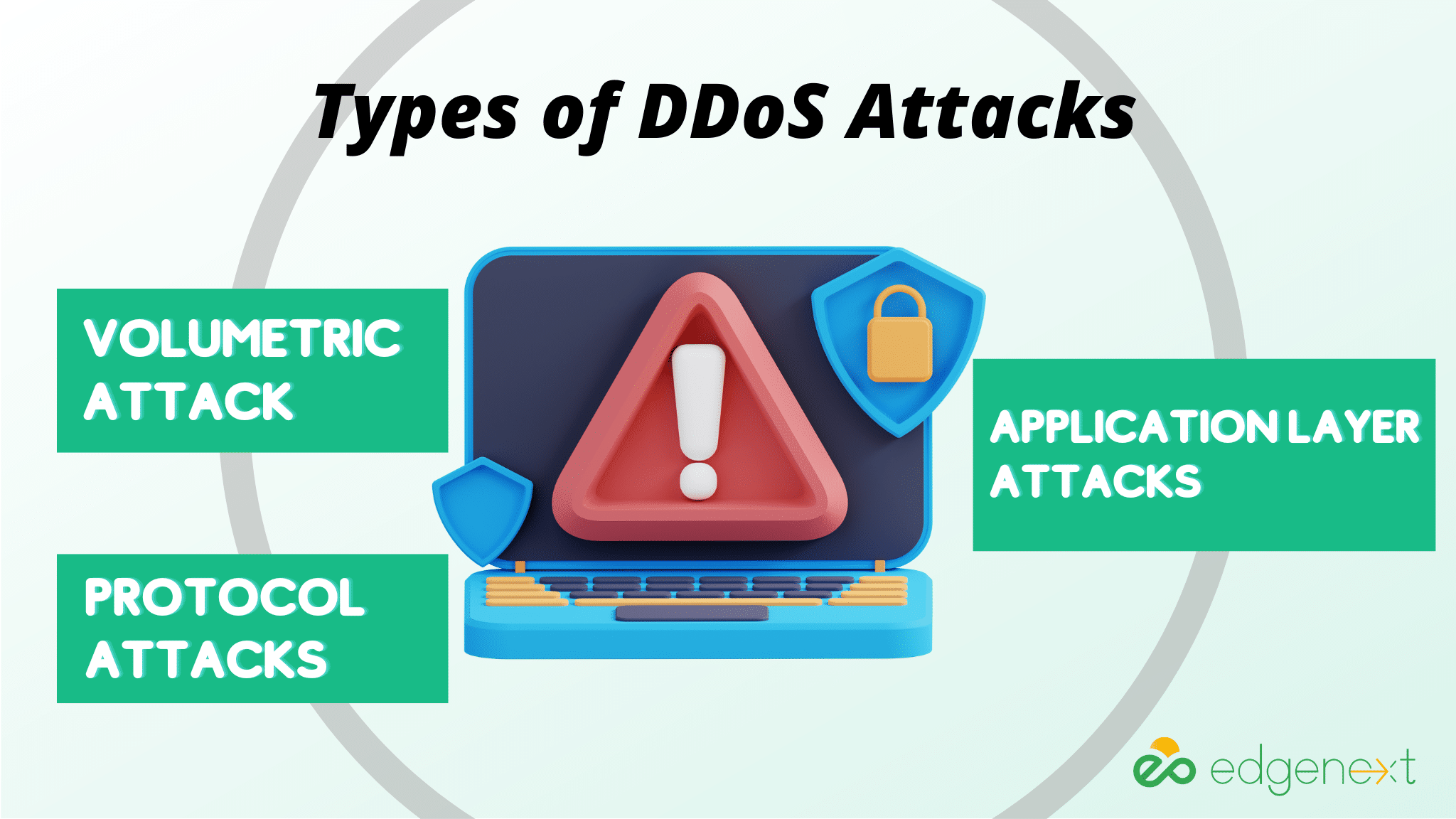
1.Volumetric Attack:
A volumetric attack is a DDoS attack involving simultaneously flooding the target with massive amounts of data or requests from multiple computers. The goal is to overwhelm the server so much that it cannot handle all incoming requests, which results in service disruption. This attack is typically used when the attacker wants to cause widespread damage or take down a website for an extended period.
2. Protocol Attacks:
A protocol attack is a DDoS attack involving sending malicious requests using a specific protocol, such as TCP/IP or UDP, to disrupt service. These attacks can be challenging to detect since they often look like regular traffic. The goal of these types of attacks is usually to compromise the server’s or application’s security by exploiting vulnerabilities in the underlying protocol support.
3.Application Layer Attacks:
An application layer attack is a DDoS attack that targets web applications by sending malicious requests to exploit known vulnerabilities. Instead of flooding the server with traffic, these attacks will send targeted requests that can be difficult to detect. Attackers often use this attack to gain access to sensitive data or cause disruption within an application or service.
When defending against DDoS attacks, businesses can implement a few strategies. The first is a proper network monitoring and logging system to detect any suspicious activity quickly. Additionally, companies should have multiple layers of security in place, such as network firewalls, intrusion detection systems (IDS), and web application firewalls (WAFs), to block malicious traffic before it reaches the target system. It’s also essential for businesses to have a clear incident response plan to know how to respond quickly and effectively when an attack occurs.
DDoS attacks can devastate businesses, causing prolonged downtime and financial losses. Companies need to understand the different types of DDoS attacks and strategies for defending against them. Implementing proper network monitoring and logging, having multiple layers of security in place, and having an incident response plan are all critical steps businesses should take to protect themselves against these attacks.
We hope this blog post has given you an overview of the different types of DDoS attacks and strategies for defending against them. If you have any questions or need additional assistance protecting your business from these attacks, don’t hesitate to contact EdgeNext Security Expert. We are here to help!

© 2025 EdgeNext Copyright All Right Reserved