
WAF is a valuable tool that can help protect your web applications from malicious activities such as cross-site scripting (XSS), SQL injection, and cookie poisoning. Such attacks are the primary cause of security breaches, making it essential to have a secure defense in place to prevent attackers from accessing your data. Using a suitable WAF, you can effectively block multiple attempts to steal or corrupt your data by targeting vulnerable systems.
Web Application Firewalls (WAFs) are a critical defense layer for businesses with an internet presence. A WAF inspects traffic to and from a web application and blocks malicious requests that could jeopardize the application’s security. This blog post will discuss WAFs, how they work, and why they’re essential for protecting your business. So, whether you’re already using a WAF or considering implementing one, read on to learn more about this vital security tool.
A web application firewall (WAF) is an essential layer of protection for web applications. For web servers, a WAF provides an additional security layer to detect and block malicious traffic before it gets to the web application’s backend. By inspecting incoming HTTP requests and responses, the firewall can detect threats like SQL injection attacks, cross-site scripting attempts, malicious bots and provide real-time protection against web vulnerabilities. In addition, WAF can help secure web applications by blocking common application attack patterns like brute force attempted logins or buffer overflows. This extra support helps organizations ensure that they provide their users with the highest level of web application protection.
WAF, or Web Application Firewall, is a powerful tool used in web security solutions that helps to protect applications from cyber-attacks. It works by examining requests before they reach an application server and filtering malicious or undesirable content. WAFs, analyze all aspects of a given request, including HTTP parameters, form field values, cookies, and headers, to ensure that the request follows a defined policy set by the site and network administrators. When an incoming request breaks the rules described in this policy, it is blocked automatically. In addition to blocking malicious requests, WAFs also provide configurable alerting and reporting on anomalies so administrators can act quickly when there is an issue within their network.
Blocklist WAFs are traditional web application firewalls that use rules to block specific requests. These rules can be based on IP addresses, URLs, user agents, and other parameters. Whenever a request matches one of these rules, it is blocked before reaching the web application. The main advantage of using this type of WAF is that it allows administrators to easily configure specific conditions for blocking/denying requests from accessing their web applications.
Allowlist WAFs, on the other hand, only allow access to those requests which match specific criteria that the administrator has predetermined should be allowed. Any request that does not match this criterion will be denied access to the underlying web application. This type of firewall provides more granular control to administrators as they have complete control over which requests can access their web applications. However, it is essential to note that Allowlist WAFs can be more difficult to configure and maintain than Blocklist WAFs.
Blocklist and Allowlist WAFs are powerful security tools for protecting web applications from malicious traffic. Depending on the requirements of an organization, either type of firewall may be suitable for implementation. Considering the pros and cons is crucial before deciding which is best for your organization’s specific needs.
The difference between a web application firewall (WAF), an intrusion prevention system (IPS), and a next-generation firewall (NGFW) is in the type of protection they provide. WAFs are designed to protect web applications from malicious requests, while IPSs are designed to detect malicious activity and prevent it before any damage is done. Finally, NGFWs combine these two security measures with additional layers to provide better protection against sophisticated threats that may bypass traditional firewalls.
A WAF inspects the HTTP traffic sent to the server and enforces a set of rules defined by an administrator. The rules can be configured to allow or block specific requests based on various criteria such as URL, parameter values, HTTP headers, etc. This helps to protect web applications from malicious requests that could compromise the application’s security.
An IPS is designed to detect malicious traffic and prevent it before any damage is done. An IPS monitors network traffic in real-time and can see known attack patterns or anomalous behavior. When a malicious request or suspicious behavior is detected, the system will immediately block it.
Finally, NGFWs are next-generation firewalls that combine traditional firewall functionality with intrusion prevention systems and other advanced technologies to provide better protection against sophisticated threats that may bypass traditional firewalls. NGFWs use deep packet inspection (DPI) technology to inspect each incoming or outgoing packet for malicious content. Additionally, NGFWs can use application layer inspection, which allows them to detect threats specific to the application type. This provides extra protection and helps ensure that any malicious traffic is detected and blocked quickly.
In summary, WAFs protect web applications from malicious requests, IPSs detect malicious traffic and prevent it before any damage is done, and NGFWs combine traditional firewall functionalities with intrusion prevention systems and other advanced technologies for better protection. Each security solution serves a different purpose and should be considered when implementing a comprehensive security strategy.
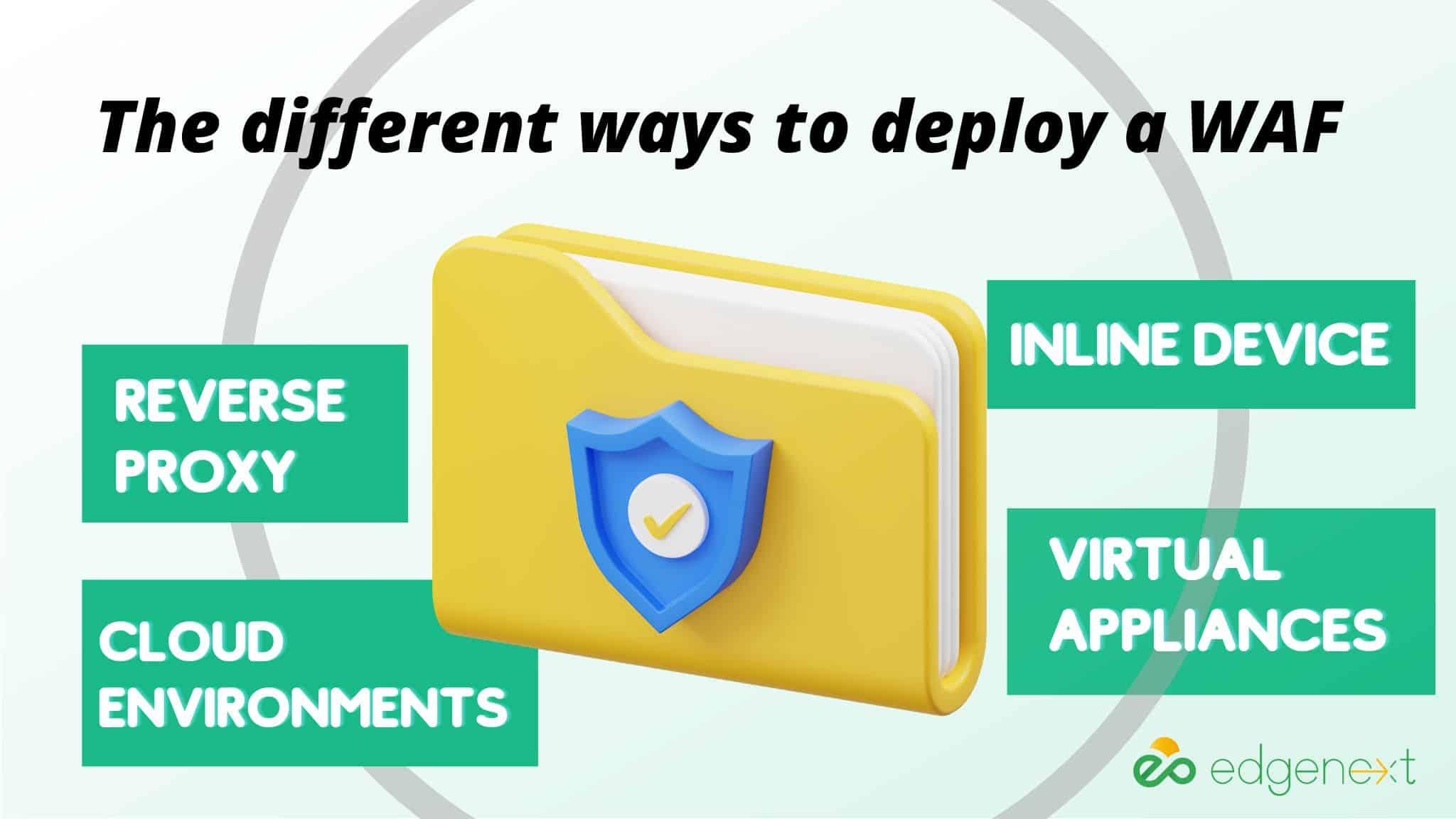
Depending on an organization’s specific needs, there are different ways to deploy a WAF. The most common way to deploy a WAF is as an inline device, meaning it sits between the web server and the internet and examines all requests before they reach their destination. This allows the WAF to block malicious requests and protect applications from cyber-attacks. Another way to deploy a WAF is as a reverse proxy, which serves as an intermediary between the web server and clients requesting content from that server. This allows the WAF to inspect incoming and outgoing traffic while keeping application-specific logic private, making it more difficult for attackers to target vulnerable areas of the application.
Another popular way to deploy a WAF is in cloud environments. This allows organizations to benefit from the scalability and flexibility of the cloud while still having a layer of security in place. Organizations can also opt for a hybrid deployment, combining inline devices and reverse proxies into one unified solution. Finally, some organizations use virtual appliances such as Barracuda Web Application Firewall (WAF), which allows them to deploy their WAF on-premises or in the cloud, depending on their needs.
No matter the deployment an organization chooses, it should ensure that its WAF is appropriately configured and tested before going live. The proper configuration ensures that the WAF will effectively filter out malicious requests while allowing legitimate traffic through. Additionally, testing is essential to ensure that the WAF is correctly configured, identifies threats, and prevents false positives.
In summary, there are several ways to deploy a WAF depending on an organization’s specific needs, such as inline devices, reverse proxies, cloud environments, and virtual appliances. Proper configuration and testing are crucial elements for ensuring adequate security protection. With the appropriate deployment method and correct setup, organizations can protect their applications from malicious actors while maintaining high availability.
A web application firewall (WAF) is essential for any website that handles sensitive information, interacts with customers or is accessible via the public Internet. WAFs protect websites from malicious traffic and cyber-attacks, ensuring the safety of customer data and protecting against data breaches. By deploying a WAF, organizations can filter out malicious requests before they reach their servers, preventing attackers from exploiting vulnerabilities in a website’s code. Additionally, WAFs can detect, and block known threats such as SQL injections and cross-site scripting attempts.
Another key benefit to using a WAF is its scalability. As the number of users on a website grows, so does the potential risk of attack; however, with a WAF in place, organizations can adjust their security settings to keep up with the changing needs of their site. Additionally, WAFs can monitor user activity and detect anomalous behavior, enabling organizations to identify problems before they cause any significant damage.
Finally, a WAF is vital to compliance with industry regulations and standards such as PCI DSS, GDPR, and HIPAA. Organizations that handle customer data must adhere to strict security guidelines; failing to do so could result in hefty fines. Organizations can ensure that their website meets these regulatory requirements by deploying a WAF and regularly auditing its capabilities.
In conclusion, utilizing a web application firewall is essential to website security. A WAF protects websites from malicious requests by filtering out malicious traffic before it reaches the server while also enabling organizations to detect and block known threats. Furthermore, WAFs are scalable, allowing organizations to keep up with the changing needs of their website as their user base grows. Finally, a WAF is necessary to comply with industry regulations and standards governing customer data security. A web application firewall can help organizations protect their websites and customers from cyber-attacks. If you’re running a website, make sure you have a good WAF in place to help protect your visitors! If you need help choosing or configuring a WAF for your site, our team of experts at EdgeNext are here to help. Contact us today and let us take care of the rest.
© 2025 EdgeNext Copyright All Right Reserved