
DDoS protection is a type of cyber security that aims to protect websites and networks from DDoS (distributed denial-of-service) attacks. DDoS protection filters out malicious traffic, preventing it from reaching the intended target. DDoS cloud scrubbing services and CDN-based web protection block attack traffic and provide DDoS protection. Cloud security solutions can also be employed as an additional layer of DDoS mitigation. By implementing DDoS protection strategies, businesses can ensure their systems are safe from DDoS attacks and retain continuity of operations.
I. Introduction: DDoS Attacks – What Are They?
II. DDoS Protection – What Does It Do?
III. DDoS Mitigation Providers – How Do They Work?
IV. DDoS Attack Prevention Strategies
V. Conclusion
DDoS, or distributed denial of service, is a cyberattack that makes a website or network resource unavailable by flooding it with malicious traffic so it cannot operate. DDoS attacks are becoming increasingly popular as attackers look for ways to disrupt businesses, organizations, and individuals online.
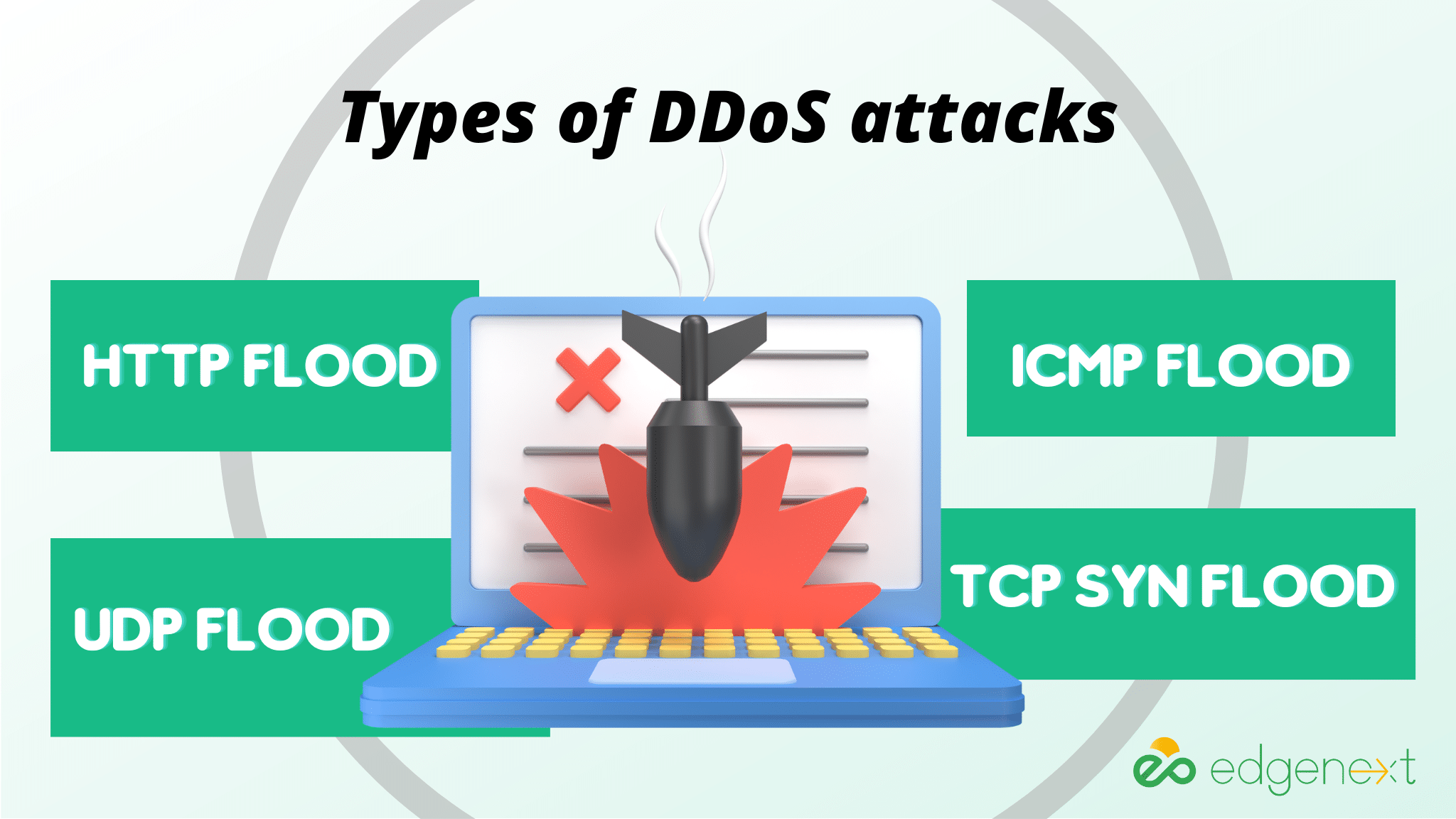
A DDoS attack overwhelms its targets with unwanted internet traffic, so the normal traffic cannot reach its intended destination. The goal of DDoS attackers is usually to shut down online services or resources, either temporarily or permanently. DDoS attacks can be categorized into different types based on their attack methods, such as HTTP flood, TCP SYN flood, ICMP flood, and UDP flood.
Some examples of famous DDoS attacks in the past include the Dyn DDoS attack of
2016 that was launched against a DNS provider called the DDoS attack on Dyn, the Mirai DDoS attack of 2016, which caused significant disruption to several major websites and services, and the GitHub DDoS attack of 2018 that targeted GitHub. These DDoS attacks have had severe consequences for businesses and individuals, with loss of reputation, customers, data, or even money.
By understanding DDoS attacks and their different types, businesses and individuals can better prepare themselves to protect their online assets from these cyberattacks.
DDoS protection is essential for businesses and individuals to protect their online assets from Denial of Service attacks. Depending on the user’s needs, DDoS protection solutions can be on-premise, cloud-based, or hybrid.
The features of DDoS protection offerings vary but typically include anti-DDoS services such as DDoS mitigation and scrubbing, which filter out malicious traffic before it reaches the target by blocking known attack sources. Advanced DDoS protection solutions also use behavioral analysis to detect and mitigate new threats.
When considering DDoS protection options, it’s essential to consider both software and hardware solutions. Software solutions are usually easier to deploy and maintain since they don’t require special hardware, while hardware solutions typically provide better performance and more comprehensive DDoS protection.
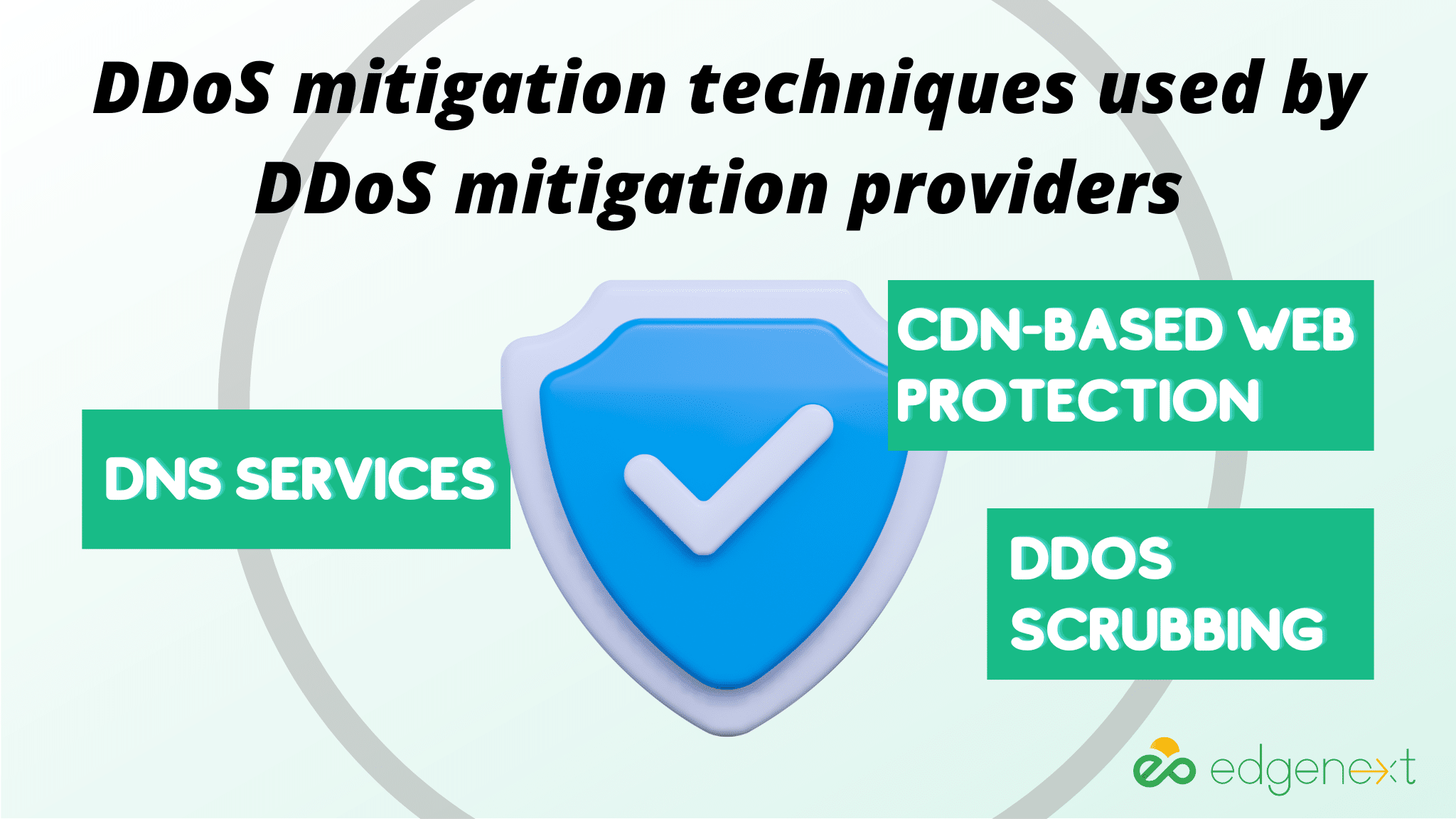
DDoS mitigation providers specialize in providing DDoS protection to businesses and individuals. These providers use different techniques to mitigate DDoS attacks, such as DNS services, cloud-based DDoS scrubbing, and CDN-based web protection.
DNS services are one of the most common DDoS mitigation techniques used by DDoS mitigation providers. This service redirects traffic from a website or network resource to another server where malicious traffic is filtered.
Cloud-based DDoS scrubbing is another popular method used by DDoS mitigation providers. It directs suspected DDoS traffic to a “scrubbing center” where malicious traffic is filtered out before it reaches its intended target, allowing only legitimate traffic to pass through.
CDN-based web protection is a third DDoS mitigation solution that can be used to protect websites from DDoS attacks. This service distributes requests for content to multiple servers across different locations to process so that attackers cannot easily overwhelm a single server or site.
Overall, DDoS mitigation providers offer a variety of DDoS protection solutions that can help businesses and individuals protect their online assets from DDoS attacks. The benefits of DDoS protection are evident in the wake of recent DDoS attacks, making it essential for anyone with an online presence to consider utilizing DDoS mitigation services.
DDoS attack prevention is essential for businesses and individuals who want to protect their online assets from DDoS attacks. DDoS protection tools such as firewalls, intrusion detection and prevention systems (IDS/IPS), DDoS monitoring solutions, DDoS mitigation techniques, best practices, and user education are all crucial components of a comprehensive DDoS attack prevention strategy.
Firewalls can filter malicious traffic, while IDS/IPS systems detect and alert administrators about suspicious activity in the network. DDoS monitoring solutions provide real-time visibility into DDoS attacks so that users can take immediate action when necessary. DDoS mitigation techniques such as rate limiting or traffic throttling are also effective tools for reducing the impact of DDoS attacks on target systems and networks.
Lastly, DDoS attack prevention requires user education about DDoS threats and best practices for DDoS protection. Employers and their employees should be aware of the risks posed by DDoS attacks and how to protect their online assets. Additionally, user education can ensure they understand DDoS attack methods and the techniques to detect DDoS activity within the network promptly.
Ultimately, DDoS attack prevention strategies are essential for businesses and individuals who wish to protect their online assets from malicious actors. By leveraging the right tools and following best practices, organizations can reduce their exposure to DDoS attacks while ensuring their assets remain secure.
In conclusion, DDoS attacks are a significant threat to businesses and individuals who have an online presence. DDoS mitigation providers offer a variety of DDoS protection solutions that can help protect against these attacks by redirecting malicious traffic away from the targeted system, filtering it through cloud-based DDoS scrubbing, or using CDN-based web protection. DDoS attack prevention strategies should also include tools such as firewalls, intrusion detection and prevention systems (IDS/IPS), DDoS monitoring solutions, and user education on DDoS threats. Ultimately, DDoS protection is essential for online data security and protecting businesses and individuals from malicious actors.
Time to Gear Up! Contact EdgeNext Cloud Security Expert Today!
© 2025 EdgeNext Copyright All Right Reserved